You are using Twitter, right? If you have used the social networking service for a while, you are well aware of the hiccups it has had through its existence. Compared to some other sites, there haven’t been too many, but still there have been enough to make the average Twitter addict annoyed out of their skull. The hiccups vary from simple service overloads (also called the “Fail Whale“) to the truly annoying malware that every so often hits the stream we are following and the direct messages we receive.
Even though most of these are spotted quickly, they still cause some people quite a bit of distress and worry. After all, stressing about losing control of an account that you have been working on for a while is going to be quite gruesome, especially if you don’t know who seized control over it. But as with all good things, it’s only a matter of time before you get it back. My experience with Twitter is that they are quite fast and the support is more than happy to help bring back the account to your possession.
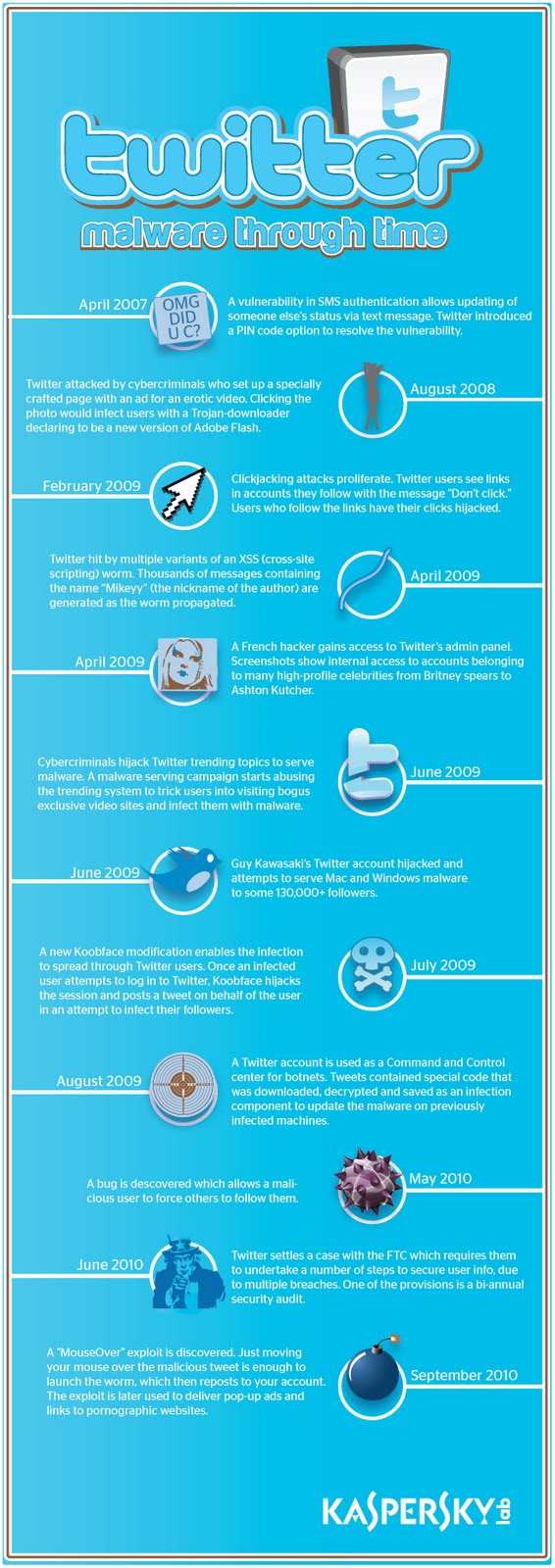
If you would like to delve deeper into the pond of hiccups that Twitter has had through the years, or rather the malware that has haunted the service, then you should be quite happy to know that Kaspersky Lab put together a complete timeline of all the malware that has shown their faces on Twitter since its birth. Maybe this kind of information isn’t exactly something you want to remember, but the fact that they are all now put in a timeline really exposes the fact that Twitter has been spared from the heavy and troublesome masses of malware that keep flooding the Internet wherever you go.
Even though the information is sometimes alarming, as a Twitter addict, I really find this stuff quite mesmerizing since there are several things I didn’t know. That brings more light into the service Twitter provides. The most alarming thing is that a French hacker gained control of Twitter’s admin panel and was able to see that Twitter had direct access to high profile Twitter users accounts and was monitoring them. It’s, of course, fully understandable that they “have” access to our accounts, after all, they are providing the service. However, it’s alarming that the accounts were monitored and visible from the Twitter admin panel. But then again, this was back in April, 2009. #ThingsChange
COMMENTS