The ransomware virus is a common type of computer virus that has been there for many years. It comprises numerous variations. Famous ransomware viruses are MRCR, Merry Christmas, Umbrecrypt, Hydracrypt, Cryptolocker, GandCrab, and Teslacrypt.
A lot of ransomware viruses can now be decrypted with a specific decryption program. Security developers are continually coming up with new decryption techniques. Myspybot.com offers a list of currently available decryption tools
On their turn, the ransomware creators are also always evolving. For this reason, it is difficult for an average computer user to know how to fight back if their files get encrypted with this malicious virus. Fortunately, there are som methods anyone can use to decrypt files infected by the ransomware virus.
How Ransomware Encrypts Files
Encryption can be defined as the process of encoding data in a way that makes it only accessible to authorized parties. The ransomware virus encrypts computer files with a key that is only known to the cyber crook who sent the virus. Once the infection is deployed, it runs a set of processes on the infected computer creating encrypted copies of original files.
The virus then deletes the original files leaving the copy file appearing as though it is corrupt. Once the encryption process completes, the virus will generate a decryption key, which is always private and know only to the attacker.
Once a ransomware virus encrypts your files, the user cannot access the data or the system. The main goal of the ransomware developers is to demand a ransom from infected users for getting back a decryption key. In the 1980s, ransoms were required to be paid using snail mail. Today, payment is demanded using cryptocurrencies like Bitcoin or a very private one called Monero.
How Does One Get Infected With Ransomware?
Malicious spam email messages are the most common method used by hackers to deliver the virus. The virus is encoded in an attachment, such as a PDF file or a Word document. Weblinks are also used to redirect the user to a malicious site. Malspam makes use of social-engineering methods to lure unsuspecting victims into clicking on the links or downloading the attachments.
Online scammers can impersonate the FBI or a security unit to scare the recipient into paying a large sum of money as ransom. They can also pretend to be a bank worker or even your boss. The good news is, you do not always have to pay the ransom to cybercriminals. There are steps you can follow trying to recover your files.
Guide: How To Decrypt Ransomware
Method 1 – Restoring Files Using Data Recovery Software
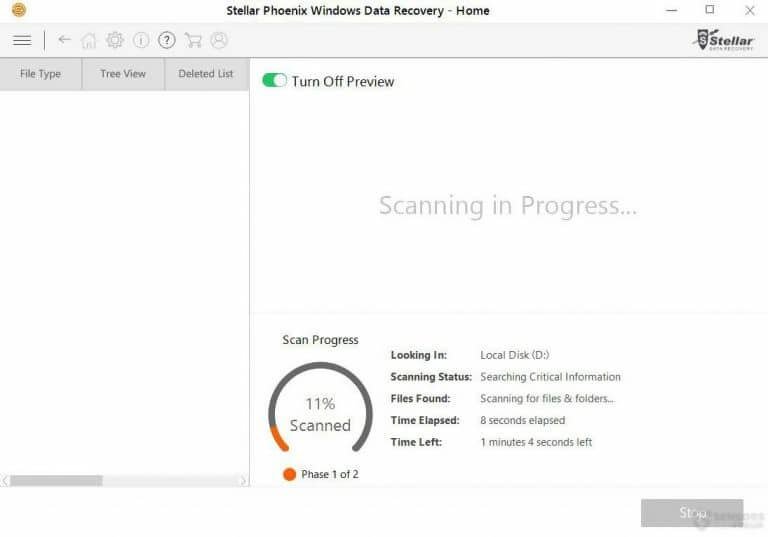
This method is ideal for ransomware viruses with no available decryption tools available. Do not format your hard drive when recovering files using a recovering software. This can significantly reduce the chances of recovering the data. There different recovery tools. I use the Stellar Phoenix Windows Data recovery.
- Download the recovery software
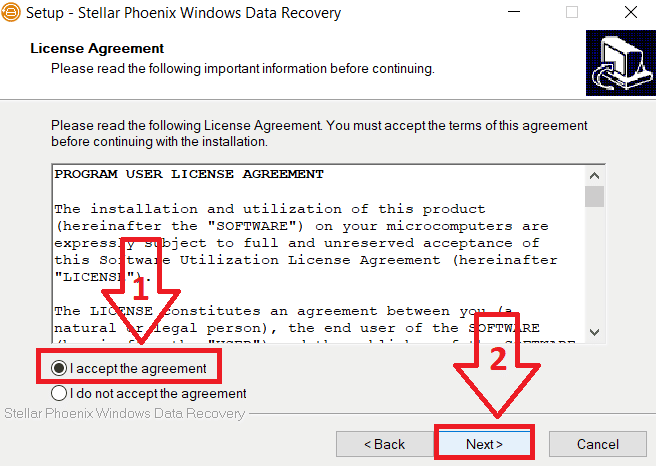
- Agree with the user license and wait for the setup to complete before clicking on the finish button
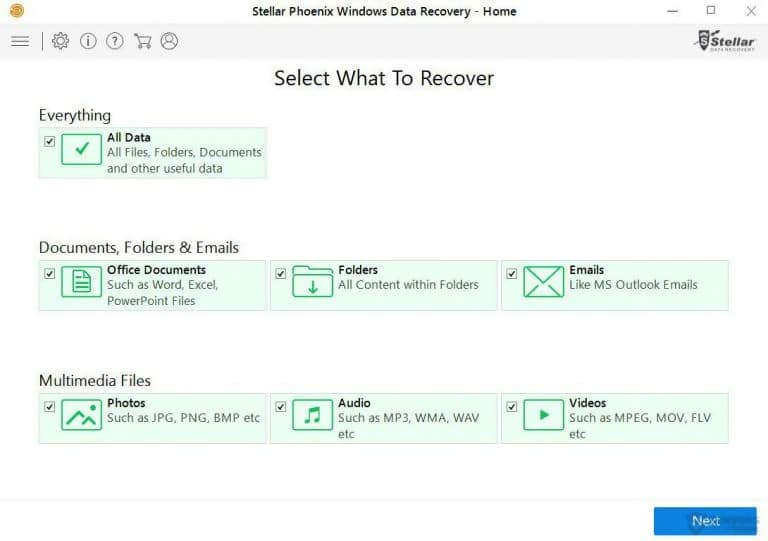
- He program will start automatically. Select the file types to recover and click on Next
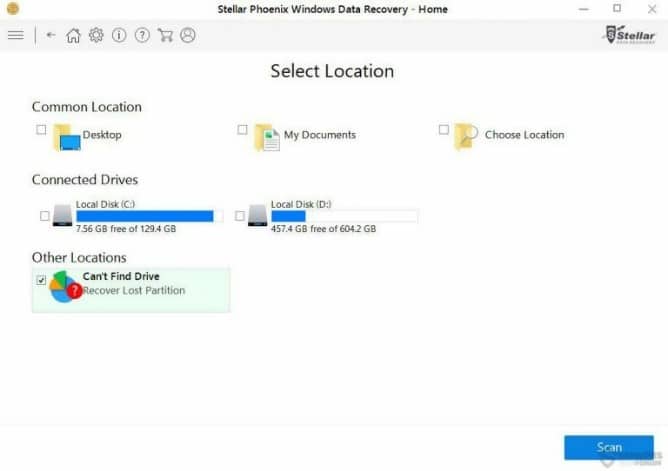
- Select the drive to use to scan the file and click on Scan
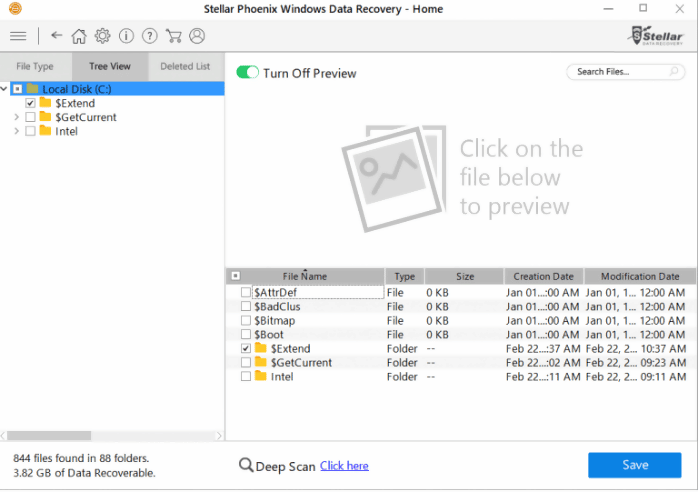
The software program will scan for files. This may take some time. Once the scan is complete, the software will open a file explorer with a review of the records you want to recover.
Once you click on the files, they will be restored.
Method 2 – Using the Windows Backup And System Recovery Mechanism
This decryption method is ideal for a situation where the Windows backup system was active at the time of the virus attack. Windows backup and recovery is the most used decryption method when it comes to ransomware.
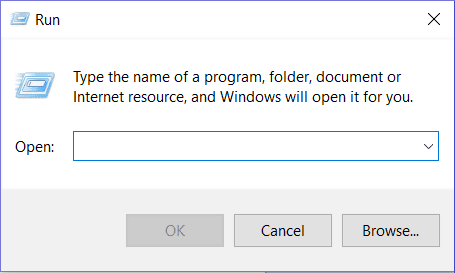
- Press the Windows button + R key to open the Run window.
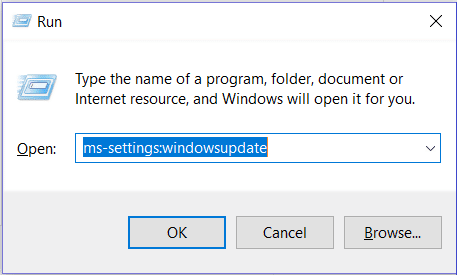
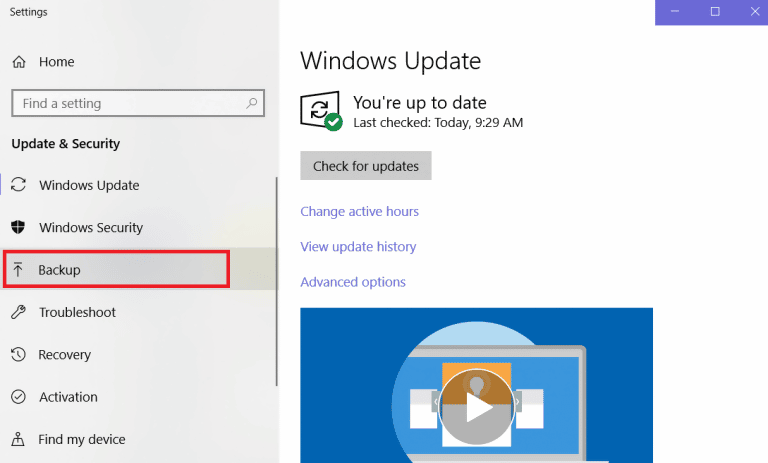
- Type in ms-settings: windows update and click on the OK button.
- On the Setting window, click on the Backup icon.
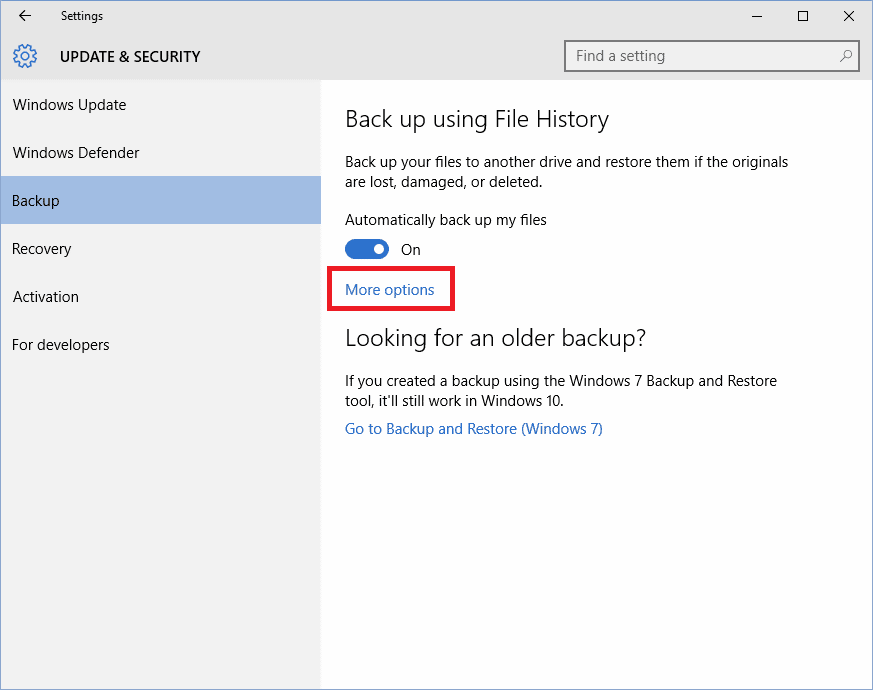
- Go to More options from the Backup page.
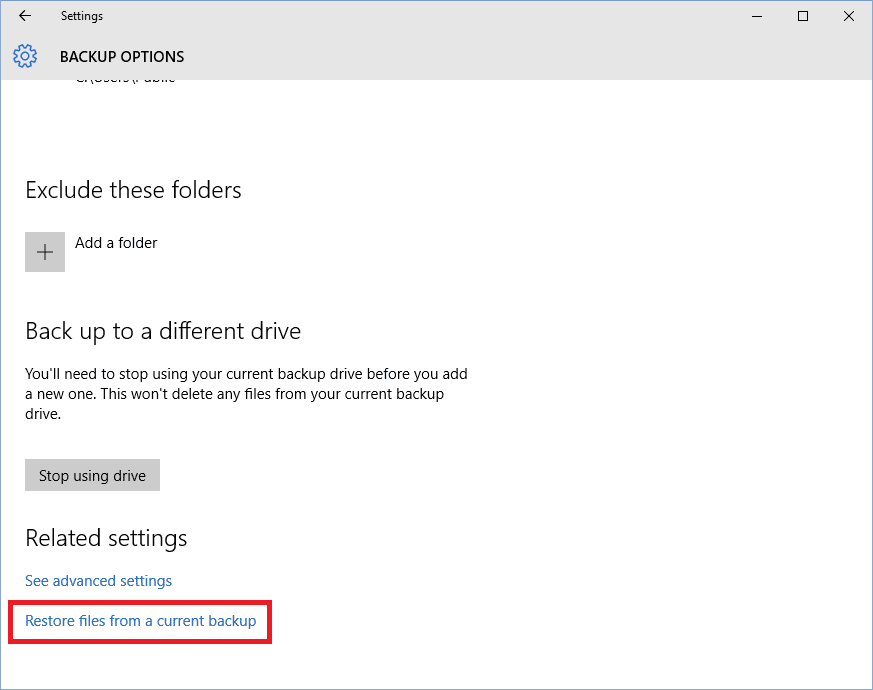
- Click on the Restore files from a current backup.
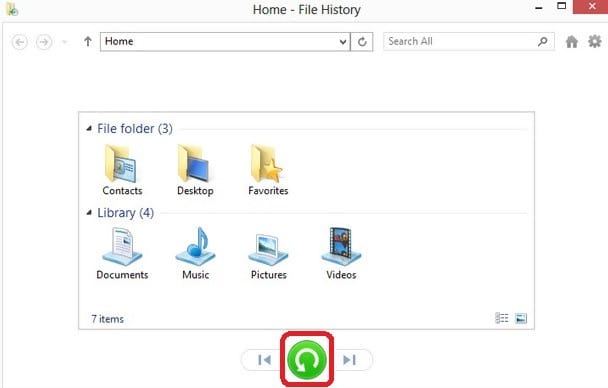
- Select the files you want restores and click on the Restore button.
This will restore the previous versions of your files.
Method 3 – Restoring Files By Plugging Hard Drive To Another Computer
This method is very straightforward. It requires you to connect your hard drive into another computer to recover your files. It is ideal for ransomware viruses that lock the user out of access to Windows programs.
- Remove the battery from your laptop or unplug a desktop computer from the power source.
- Unscrew the hard drive case of the computer or notebook.
- Plugin the hard drive on a secure computer. The OS will detect the hard drive as a separate partition.
- Use a recovery program to gain access to the folders on the hard drive without typing in the Windows username or password.
Whichever method you decide to use, you should be able to recover and decrypt your files. In the future, take relevant measures to avoid downloading a malware program on your computer.
If you are interested in even more technology-related articles and information from us here at Bit Rebels, then we have a lot to choose from.



COMMENTS