If you want to eliminate most of the computer threats you are constantly faced with, you will have to educate yourself in the ways that hackers get a hold of your data. I know, I have said this before, and it’s always the same thing. Well, not exactly. Hacker tactics evolve on a daily basis, and if you want to stay somewhat secure, you will have to stay up to date with the ways they constantly change their tactics. We all want to hacker-proof our lives as best we can.
If you do this, it’s not the same thing as completely eliminating all computer threats. That would be almost impossible to do since technology constantly evolves, and with the positive comes the negative aspects. Hackers try to get a hold of you private data because they want to use it for their own benefit. It usually comes down to stealing money directly or fraudulently gaining it through some other way of forging your identity. When you hacker-proof your private information, you at least make it harder for hackers to gain access to your data.
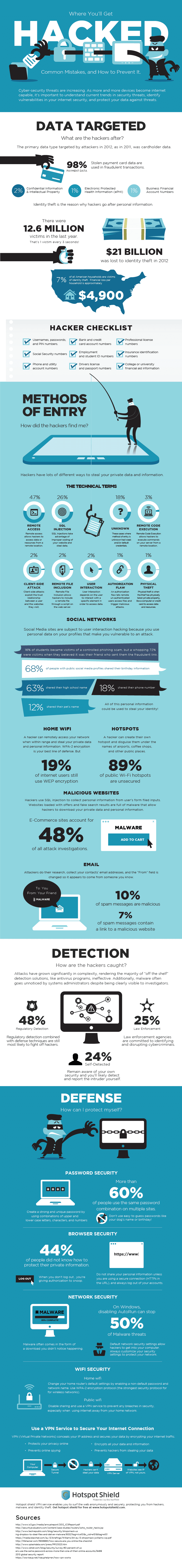
Now here’s the kicker that might put your mind into a tale spin of gigantic proportions. Did you know that 89% of all public hotspots are insecure? This means that someone who knows what he or she is doing could use a “sniffer” to gain access to the information sent through the wireless connection you have established. That means that when you are browsing, paying bills or talking to your friends on your favorite social networking services, this particular individual could see everything you’re doing. This of course means that once you punch in that password to your private information, they will have it. If we take all possible precautions and hacker-proof our gear and content, we run a much smaller chance of actually being hacked.
I can’t stress it enough…creating a strong password for sites and services where you store your personal and private information is the most important thing, and it goes a long way to hacker-proof your stuff. Furthermore, don’t use the same password for every service you use. Picture this, if you have the same password for all your services, what if someone gains access to one of those services? What would most likely happen is that all of your accounts will be breached, and you will be left with nothing less than a mess that will take you weeks to resolve. It’s time and money lost, not to mention the heartache caused from knowing someone now has all your personal information. That just won’t cut it.
It’s quite easy to stay up to date with security risks and how to prevent and hacker-proof your stuff, or even to just make it harder for someone to gain access to it. This infographic called Where You’ll Get Hacked: Common Mistakes, And How To Prevent It, presented by Hotspot Shield VPN, is a formidable resource to educate yourself about how to hacker-proof your information and prevent it from ending up in the wrong hands.
Once you know your own weaknesses, it’s quite easy to patch them up, even if only for a while. As I said in the beginning, staying up to date with new hacker tactics is vital if you want to keep your private information safe from hackers. Always hacker-proof your stuff, even if it means just changing your passwords from time to time.
How To Hacker-Proof Your Life
(Click Infographic To Enlarge)
Via: [visual.ly]
COMMENTS