In recent years, cloud computing has emerged as a disruptive technology for businesses, as it provides a variety of benefits that have prompted a quick uptake of the technology.
For example, instead of depending on personal computers or local servers to store, manage, and process data, businesses may now use a vast network of remote servers hosted on the Internet, thanks to cloud computing. This allows businesses to store, manage, and process data much more efficiently.
Because of this, businesses are able to increase their speed and adaptability while also cutting costs connected with the management and maintenance of their own internal information technology infrastructure.
IMAGE: UNSPLASH
However, as more and more businesses shift their data and applications to the cloud, it is becoming necessary for such businesses to give careful consideration to the safety of their data.
The activity of ensuring that data and applications stored in the cloud are protected against unauthorized access, theft, and other security concerns is called cloud security. To strengthen this protection even further, many organizations now integrate advanced SIEM solutions to monitor threats in real time.
In light of the growing number of cyber attacks and data breaches, businesses have no choice but to put in place stringent safety precautions in order to guarantee the integrity and safety of their most important data stored in the cloud. This involves encrypting data both while it is in transit and while it is at rest, controlling access to the data and authenticating users, and performing regular audits and assessments of the security of the system.
Leveraging SIEM For Proactive Cloud Security
As the occurrence of cyber attacks and data breaches continues to rise, it has become imperative for businesses to implement stringent security protocols to perform cloud data security.
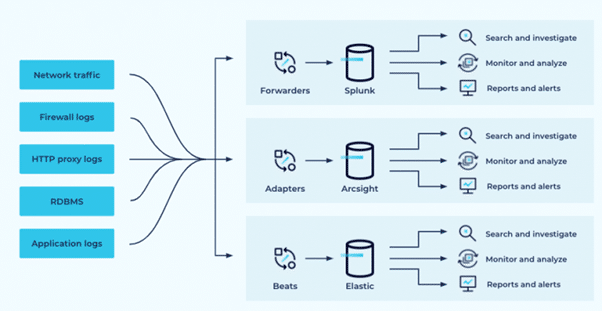
The term “Security Information and Event Management” (SIEM) refers to a technology that has evolved into an indispensable resource for businesses that want to ensure the safety of their data and apps hosted on the cloud. It is a tool that detects and responds to security incidents by collecting and analyzing data related to security from a variety of sources, such as network devices, servers, and applications, in order to improve security.
By utilizing SIEM, businesses can proactively monitor their cloud environments and respond immediately to any security concerns that may arise. This allows businesses to stay one step ahead of any potential security incidents and guarantee the safety and security of their cloud-based products.
The capability of SIEM to give centralized visibility and management is among the most significant advantages that it offers for cloud security.
SIEM solutions have the ability to integrate data pertaining to security from a variety of sources, providing a uniform view of an organization’s security posture in the process. This makes it simpler for security teams to notice, investigate, and respond to security issues. It also helps to ensure that any security concerns are addressed as quickly and effectively as possible.
IMAGE: CONFLUENT
Benefits Of Using SIEM
SIEM offers a wide variety of advantages that may be enjoyed by its users. It provides a centralized approach to logs and enhances visibility in the process. Additionally, it assists in regulatory and compliance matters and early detection of threats and attacks. Let’s discuss them in detail.
Centralized Visibility Of All The Resources
This is widely regarded as one of the most significant advantages that SIEM offers. It offers consolidated visibility and control so that you can access and control everything from a streamlined dashboard.
This is a significant advantage. SIEM can give a holistic view of an organization’s security posture by consolidating security-related data from numerous sources that are deployed, such as from servers, CDN, instances, and firewalls, among other components.
Since all of the data is displayed in a centralized dashboard, and engineers are not required to check the logs for each component, it makes it easier for security teams to detect, investigate, and respond to security incidents that occur. Additionally, it helps to ensure that potential security threats are addressed quickly and effectively because it can be combined with the appropriate triggers or alerts.
IMAGE: CONFLUENT
Minimizing Threats Detection With Better Response Time
SIEM provides real-time threat detection for cloud computing security. Real-time identification of potential security breaches is one of the many uses that can be put to SIEM’s combination of machine learning algorithms, behavioral analysis, and correlation rules.
A business can gain additional knowledge regarding potential dangers and incidents by employing a variety of log filters and establishing diverse connections between the data they collect.
These queries can be modified to fit the user’s requirements, and the backup can be kept for an extended period. It has a very low response time in terms of EPS (event per second), which not only helps improve efficiency but also makes it possible to perform searches quickly. It is capable of storing all kinds of logs.
Conclusion
SIEM is a vital tool for enterprises to protect their data and apps in the cloud. SIEM is an approach to information security that provides organizations with centralized visibility and management, detection of threats in real time, increased security intelligence, and support for compliance. This makes SIEM a comprehensive method of protecting information.
SIEM is a crucial tool that helps organizations protect their key data, minimize their exposure to cyber risks, and maintain the confidence of their customers and stakeholders.
As the number of cyber attacks and data breaches continues to rise, this technology has become increasingly important. SIEM provides multiple vital benefits for cloud security, and businesses that adopt SIEM solutions are in a better position to protect their sensitive data and remain secure in the face of an ever-evolving threat landscape.
IMAGE: UNSPLASH
If you are interested in even more technology-related articles and information from us here at Bit Rebels, then we have a lot to choose from.


COMMENTS