Cross-site Scripting (XSS) is listed on the second spot in CWE Top 25 Most Dangerous Software Errors, which got refreshed this year after eight years. XSS jumped two positions in the list — from fourth in 2011 to second in 2019. That means Cross-site Scripting (XSS) bugs are super-critical vulnerabilities.
This brings us to the question: how to avoid these bugs? There are numerous methods to avoid making such mistakes in your apps or websites. But first, you must understand the reason for the occurrence of such bugs. That said, let’s get to know the role of open-source software in introducing bugs in your software.
IMAGE: PEXELS
What Is Cross-Site Scripting?
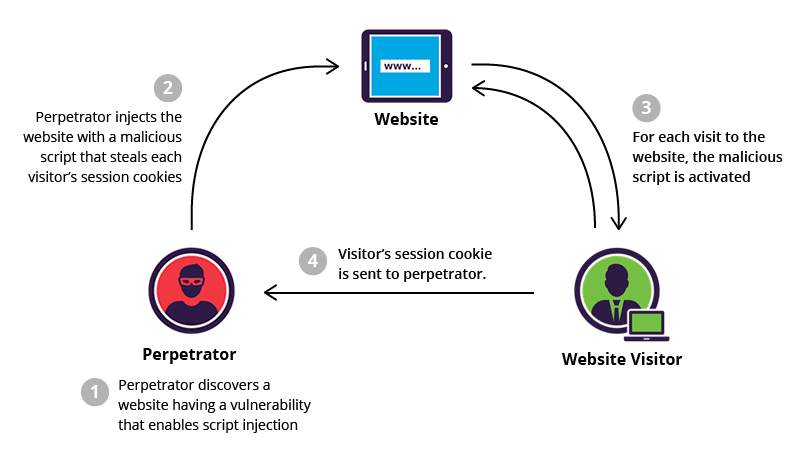
Let’s start with getting to know Cross-site Scripting (XSS). Cross-site Scripting is a type of software vulnerability in which an attacker executes malicious code on the client-side, i.e., in the user’s browser. The scripts can be injected into an app or website using any method, but the real attack occurs when a user visits the compromised web app or website; then, the code gets executed!
The websites with no or poor input sanitization are the primary targets. The attackers load malicious code in these sites, say a forum or message board. The malicious code usually performs actions on the user’s behalf. For example, an attacker may inject code in a banking app to transfer any money from the user’s account to the attacker’s account by forging the send-to-account info.
Also, Cross-site Scripting bugs are prevalent. They’re found in a variety of software — web apps and sites to desktop and mobile apps. It’s no wonder that XSS bugs were recently discovered in the popular email apps: Gmail and Outlook.
1. Cross-Site Scripting Bug In Gmail
“In a blog post, Bentkowski said the security flaw was present in AMP4Email, a feature in Gmail pushed out to general availability in July. AMP4Email, also known as dynamic email, was implemented to make it easier for dynamic content to show up in emails, such as comment threads or event invitations,” per ZDNet.
2. Cross-Site Scripting Bug In Outlook
“The bug (CVE-2019-1460) would allow an attacker to perform cross-site scripting (XSS) attacks on the affected systems and run scripts in the security context of the current user, according to Microsoft’s advisory on the bug. In this case, the computing giant said that the issue exists in the way Microsoft Outlook for Android software parses specifically crafted email messages – thus, an attacker could exploit the vulnerability by sending just such an email,” wrote Threatpost.
How OSS Introduce Vulnerabilities
Open-source software is believed to have fewer bugs than proprietary software. Why? Everyone assumes that a developer community backs open-source software, so the bugs are discovered and fixed faster than their proprietary competitors. In some cases, it’s true, but in many cases, this isn’t the case.
CSO Online reports that the most popular apps can have security vulnerabilities. Then, those vulnerabilities may get ignored or missed by their developers, as well. Sometimes, they go unnoticed — they’re unknown to the developers as well as the attackers. However, it may not be the case for every security vulnerability. Maybe a few of such vulnerabilities are known and used by cybercriminals.
For example, QEMU’s (a free and open-source emulator) VENOM vulnerability — introduced in 2004 — got fixed after 11 years in 2015. Then, IE6’s (Microsoft Internet Explorer) Flash exploit was fixed after 12 years in 2014. Similarly, Bash’s (Linux and Unix’s shell) Shellshock bug was fixed after 25 years in 2014, sadly!
Examples Of OSS Introducing XSS Bugs
Let’s check some recent examples, wherein, an open-source library or solution resulted in Cross-site Scripting bugs. You’ll be amazed to know that some of the most popular software that runs on millions of websites are known to have Cross-site Scripting (XSS) vulnerabilities, causing severe issues for them.
jQuery — The Popular JS Library
jQuery is one of the most popular libraries for creating dynamic web apps and websites. Although it’s superseded by single-page application technologies like Angular and React, it’s still used by 73% of the sites scanned by W3Techs.
Synk — a security company that helps developers create secure apps — tracked six security vulnerabilities in jQuery. It tracked the multiple versions of jQuery — from v1 (its initial release) to the recent versions. It reports that if you’re not using jQuery 3.4.0 or above, your web app or website is vulnerable to four Cross-site Scripting vulnerabilities and two other security bugs, sadly!
“W3Techs reports that of all websites using jQuery, it’s 1.x release is dominating with 83.4% of share and version 2 and 3 lag far behind with roughly 8% of all jQuery usage. When looking at the known security vulnerabilities and map them out to jQuery versions we found that four medium severity Cross-Site Scripting vulnerabilities are affecting jQuery v1 which is potentially concerning considering the 83.4% market share for anybody not employing software composition analysis to find and fix vulnerabilities in their open source components,” according to Synk’s The State of JavaScript Frameworks Security Report 2019.
Magento — An E-commerce Platform
Magento — now acquired by Adobe — is a popular platform for building e-commerce stores. It offers an open-source version that anyone can download and host on his server to launch an online store. It’s the third most popular platform, which powers 9% of all e-commerce stores on the planet.
In March 2019, Magento released security updates to fix 37 bugs in its enterprise and open-source e-commerce platforms. What’s surprising? There were 16 XSS bugs out of a total of 37 bugs that were patched in the security update.
“Magento Commerce and Open Source 2.3.1, 2.2.8 and 2.1.17 contain multiple security enhancements that help close Remote Code Execution (RCE), Cross-Site Scripting (XSS), and other vulnerabilities,” according to Magento Security Center.
That’s all about how and why open-source software may introduce security vulnerabilities in your software. You must opt for Software Composition Analysis (SCA) tools to create an inventory report on the open-source components in your software. The report shows outdated components and required security fixes for keeping your software secure from vulnerabilities, including XSS bugs.
If you are interested in even more technology-related articles and information from us here at Bit Rebels, then we have a lot to choose from.


COMMENTS