Search query: cyber security
How Are Tech Experts Protecting Themselves Against Cybersecurity Threats?
Cybersecurity continues to be a big threat to the smooth operation of businesses, including those operating in the tech sphere. The Annual Data Breach Year-End Review by the Identity Theft Resource Center saw a 44.7% increase in the number of cyberattacks in a two-year period. During the COVID-19 pa ...
Why Do Businesses Need To Level Up Their Cybersecurity?
In today’s modern world, almost every business entity leverages digital technology for a variety of purposes that can include production, distribution, and marketing to name a few. This entails the need for a business to store and transmit digital information over various networks that encompass the ...
Thierry LeVasseur, Vancouver Internet Security Expert Describes Four Types Of Cyber Attackers
One of the most debilitating occurrences that can happen to you or your business is discovering that your computer has become the victim of a cyber attack. There are best defenses practices you can take against an attack from occurring, such as implementing strict policies, employee education and c ...
Everything You Need To Know About Creating A Cybersecurity Plan To Protect Your Small Business
Does your small business have a cybersecurity plan? Here’s how to create one that will protect your business from cyber risks and threats large and small.
How To Create A Cybersecurity Plan to Protect Your Small Business
You know that as a business owner, you must ensure the cybersecurity of your ...
Automated Lifecycle Management Improves Cybersecurity Protections
Understanding the principles of automated lifecycle management and employing them to create a cyber secure data system should be a priority for your business.
It is important to learn about the automated lifecycle management AI tools that are being utilized by businesses to develop apps and stren ...
Boosting Cybersecurity With AI – How Is It Done?
With businesses, companies as well as government facilities moving entirely online, security breaches have become one of the biggest disasters a company could face. With technological advancements evolving every second, an antivirus or firewall is no longer enough to keep your sensitive information, ...
5 Ways 3D Printing Is Susceptible To Cybersecurity Risks (And How To Mitigate Against Them)
3D
printing (also known as additive manufacturing) is making inroads into various
fields including agricultural (such as tractor parts),
industrial, civil engineering, aerospace, and medical equipment manufacturing.
But as with any positive development, there are risks.
For
additive manufacturi ...
![Why Cybersecurity Training Is Crucial For Your Business [Infographic] Why Cybersecurity Training Is Crucial For Your Business [Infographic]](https://bitrebels.com/wp-content/uploads/2018/07/cyber-security-training-header-image-optimized.jpg)
Why Cybersecurity Training Is Crucial For Your Business [Infographic]
Whilst it might go against the common perception, the greatest threats to your business are not external – they are internal. Now don’t panic, I’m not talking about industrial espionage or sabotage here! Rather, I’m talking about the potential risks that even the most trustworthy employees can repre ...

7 Reasons We Need A Serious Overhaul In Healthcare Cybersecurity
Cybersecurity in the healthcare industry has been a passing concern for hospital administrators and other high-ranking positions for years, but the need for more serious security measures is growing. As we charge headfirst into the new technologies awaiting us in 2018 and beyond, we’re going to need ...

Why Cybersecurity Training Should Never Be Overlooked
Cybersecurity is the process of identifying, responding, and stopping security breaches and other cyber incidents. Though cybercrimes can be both minor and major, there is always a negative effect on a business, individual, government, or community.
According to the Department of Homeland Securit ...
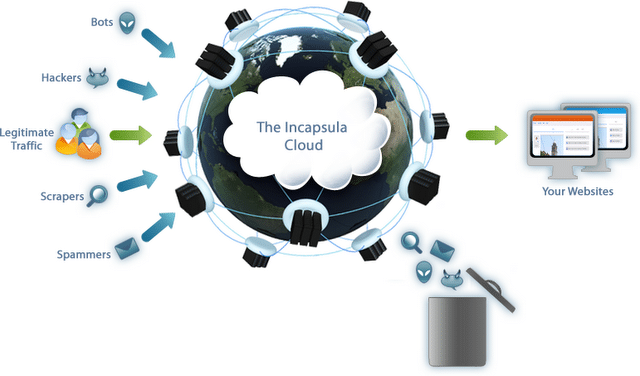
Incapsula: Website Security Protection To Keep Cyber Cyclopee Out
Recently, I wrote a bit of a rant about the ins and outs of protecting your website from Zombie hackers, malicious code snakes and spammers in Keep Bleep’n Website Zombie Hackers Out. The key takeaway was that business leaders need to embrace the fact that our websites will be attacked by one or all ...
![Obama vs. Romney On Cybersecurity [Infographic] Obama vs. Romney On Cybersecurity [Infographic]](https://bitrebels.com/wp-content/uploads/2012/10/cybersecurity-obama-vs-romney-infographic-optimized.png)
Obama vs. Romney On Cybersecurity [Infographic]
There is no doubt the American Presidential election has garnered a lot of "scandals" and news worthy events for each candidate to express and correct their positions on relevant issues. There is a lot of information to take in, and people usually settle in on one thing which sways them to vote a ce ...
Game-Theoretic Malware Detection: A Visionary Step Toward National Cyber Safety By Ashish Reddy Kumbham
During my continuous research about next-generation malware detection models, I have gotten hold of a journal article that easily stood out amongst others. The title “Game-Theoretic Malware Detection: Adversarial Neural Networks for Enhanced Real-Time Security,” by Ashish Reddy Kumbham, struck me in ...

Business Security Tips
In 2025, cybersecurity is a top priority for businesses of all sizes and all industries. However, you should not overlook the importance of general business security. Criminals still frequently target business premises, particularly those that are left vacant overnight and/or have cash, stock, and/o ...

IT Outsourcing In London: Why Cased Dimensions Leads With Military-Grade Security
As digital operations expand in complexity, London organisations face heightened challenges in balancing agility, cost control, and robust defence against cyber threats. Traditional IT outsourcing is no longer sufficient; the modern enterprise requires partners who can embed military-standard securi ...