Cloud storages represented by popular services such as Google Drive, Amazon S3, Dropbox, etc. are well known to users of mobile devices and computers. In recent years, they appear in increasing numbers. These services allow users to easily, quickly and at any time get authorized access to the files via the Internet. It should also be mentioned that the appearance and spreading of these cloud technologies were only a matter of time: qualitative improvement of technologies, namely multi-core processors, multithreaded programming, virtualization as well as the common usage of the Internet all these led to the widespread use of cloud computing in the field of information technology. For the modern world, cloud technologies provide quite a lot of advantages, and thanks to this the development of IT technologies only gains the pace.
However, the very idea of cloud computing arose in the 70’s and represented that different devices would be connected to the network, and would gain access to all the information and software. And starting from the 90’s, cloud computing technologies are becoming more and more popular. According to the Statista report, in 2017, more than 1.8 billion people used the personal cloud storage all over the world.
IMAGE: CLOUDMOUNTER
The Advantages Of Cloud Storages
The obvious advantage of storing data in the cloud is the fact that you are not bound to a certain device and can access the information from anywhere and from any system. Cloud storage is a great way to protect yourself from any emergencies. It allows you to access your data from another device if you have lost the primary one or it was stolen. However, like any other technology, there are also disadvantages, that significantly affect not only the “cloud computing” itself, but also affect those who use them.
In 2016, at the RSA conference, CSA, the leader in security standard, identified the main threats to cloud computing, namely: data leakage, compromising of accounts and authentication bypassing, the vulnerability of the used systems, insiders-intruders, advanced persistent threats, permanent loss of data, DDoS attacks.
Obviously, users have the most questions about the security of storage on external information servers. After all, there are no guarantees that the data stored on cloud servers are intact. There are already examples of cloud servers being hacked and being targets for industrial espionage.
Also, there are fears that the government itself will study and analyze these servers for its own purposes, which can negatively affect citizens (censorship and harassment from the government).
However, nowadays cloud storages pay a great attention to the security issues and provide the sufficient protection of your data. At the same time doing their best in order to increase the level of protection. Nevertheless, you shouldn’t rely on a third person concerning the protection of your information and make steps yourself.
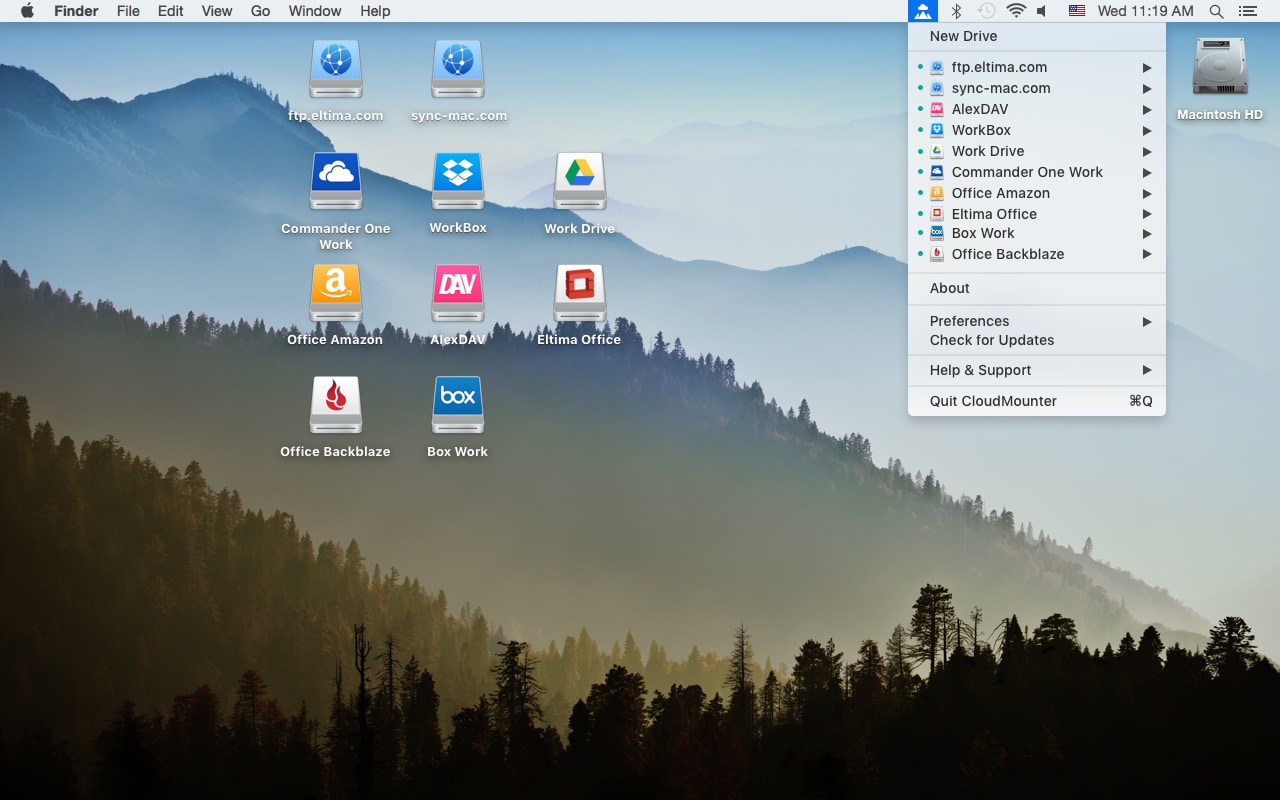
One of the ways to protect the data is encryption. If you want to protect the information properly, it is worthwhile to implement encryption at every stage of the data life cycle. Numerous solutions for encrypting data in the cloud are presented on the market. Let’s take, for example, CloudMounter, presented by Eltima Software.
CloudMounter is a well-organized app thanks to which you can mount most popular cloud storages as if they are your local disks and work with the information stored online as with the local one, at the same time, keeping it protected from any unauthorized access thanks to AES256. So, in case if your password somehow will be compromised, no one will be able to access your personal information.
Thanks to the flawless integration into Finder, CloudMounter provides you with the direct access to your online information. It’s worth noting that while using CloudMounter, there is no need to sync local files with cloud storages. Do whatever you need or want. Copy, move, open, download file to the cloud or upload from it, move files between clouds without manually copying them to your Mac. However, note that a temporary copy of the file will be stored on your computer until the operation is completed and deleted afterward.
CloudMounter works the way that all the encrypted information can be available for a person with a decryption key, making it impossible for the rest of the users to read it. n addition, CloudMounter uses standard API of cloud services. It means that the app neither store nor transmit your personal information to any third parties. All the login information from remote servers and cloud storages are securely stored in Mac OS X Keychain.
Briefly, CloudMounter can be your lifesaver and top choice if you are using several cloud storages and your SSD drive has a low storage space. Try it now and enjoy such an efficient solution.
If you are interested in even more technology-related articles and information from us here at Bit Rebels then we have a lot to choose from.
COMMENTS