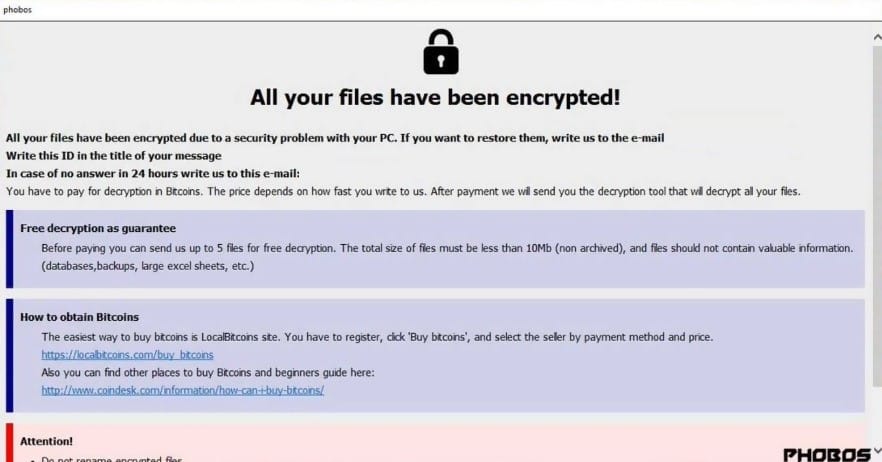
Phobos Ransomware is a file-encrypting computer virus. It corrupts all documents on a computer and displays a message soliciting for a ransom to be paid to get the decryption key. Most of the time, hackers will ask for the payment to made with Bitcoin cryptocurrency. Phobos ransomware displays the following message on the desktop:
Most of the time, files encrypted by Phobos cannot be decrypted without a decryption key. The hacker is the only one with this decryption key. Even so, since Phobos is one of the many ransomware viruses created, there may be a developer with the right tool to decrypt files. You can check online ransomware forums for possible decryption tools or dedicated malware removal sites like Soft2Secure.com
How The Phobos Ransomware Penetrates Your Computer
Phobos virus is distributed mostly through spam emails. These emails contain attachments that carry the virus. Sometimes, the Phobos virus is deployed to the computer after the hacker takes advantage of security vulnerabilities in the operating system or other software. The spam emails come with tricky headlines that force the recipient into thinking it is a legitimate email from a trusted company or government agency.
Most of the time, crooks pretend to be a DHL or FedEx. In this email, the hacker explains how they have been trying to deliver a package to you without success. The email further asks the recipient to download the attachment or click on a link to correct the shipping details.
Once the recipient clicks on the link or downloads the document, the Phobos ransomware gains access to the computer. In some cases, the Phobos ransomware can attack a computer by using the RDP -Remote Desktop Services. Hackers look for systems that use RDP and attempt to crack their passwords or ports.
How Phobos Ransomware Works
Once the virus is on the computer, it uses strong encryption algorithms to lock files and restrict the user from accessing his/her data. Once successful in this attempt, the virus attempts to extort money from the victim.
The Phobos ransomware virus targets all Windows versions, including Windows 7, 8.1, and 10. When it first installs on the computer, it creates a file with a random name in the %AppData% or %localAppData% folders. This file gets launched and starts scanning local and mapped drives finding data files to encrypt.
Unlike other ransomware viruses that encrypt all file types, the Phobos ransomware targets specific file extensions. These files include essential documents like .docx, .xls, pdf and, and others. Once infected, the virus changes the extension to ID(random numbers).(email).extension, making it impossible to open these files.
After the files are encrypted, Phobos creates info.txt ransom note. After scanning the computer, the virus also deletes shadow volume copies available. This is done to prevent the user from recovering the files from the shadow volume copies.
Once it entirely takes over the system, a pop-up window will be displayed. This pop-up window contains a message indicating that files have been encrypted. The message also includes details of how to contact the hacker and make payments.
How To Remove Phobos Ransomware From Your Computer And Decrypt Your Files
Please mind that by starting the removal process, you run the risk of losing your files. There are no guarantees that the data can be recovered. There are some programs you can use to detect and remove the ransomware. However, these programs cannot always help to recover documents or files.
Step 1 – Using A Malwarebytes Removal Program
Malwarebytes is one of the most commonly used anti-malware programs for Windows. It can get rid of numerous malware programs for free.
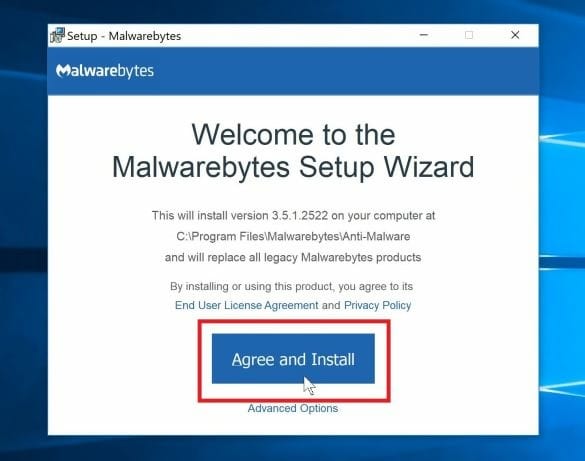
- Download the Malwarebytes program.
- Install the program following the on-screen prompts.
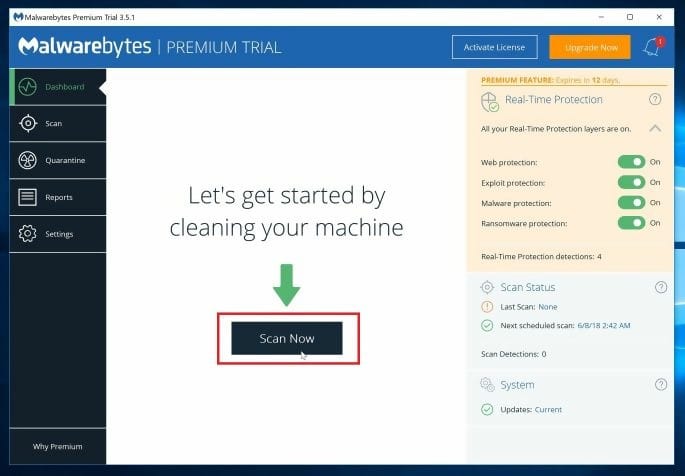
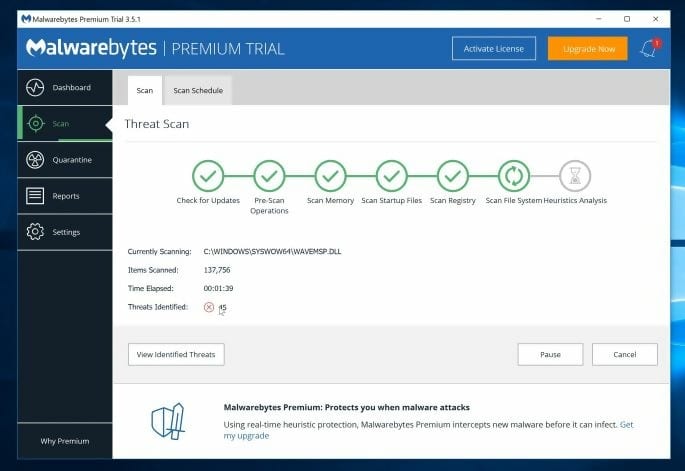
- Click on the Scan Now button.
- Wait for the scanning process to complete. This step may take a few minutes.
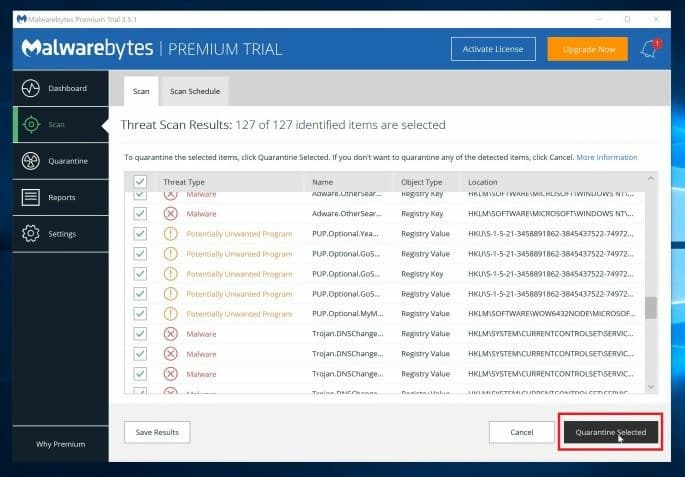
- Click on Quarantine selected to remove all malicious programs found.
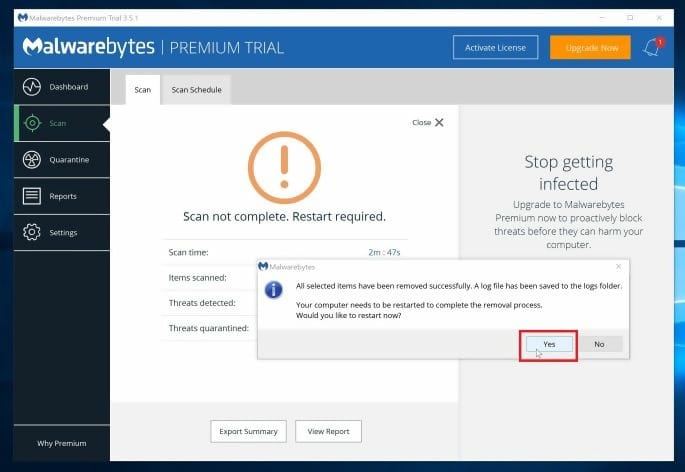
- Reboot the computer to save changes made.
This will remove the Phobos ransomware, and any other malware detected.
Step 2 – Using A Recovering Software To Restore Files Encrypted By Phobos Ransomware
Though rarely, sometimes it is possible to recover data that got corrupted as a result of the Phobos attack. This is possible in instances where the Phobos malware did not manage to remove shadow volume copies in time or if the virus was installed with bugs. This can be done by using a file recovery program such as ShadowExplorer for Windows.
- Download the ShadowExplorer program from a reliable online source.
- Install the program and follow the wizard to scan and restore the files.
Once recovered, you can download a powerful anti-virus for your device to protect it from future attacks.
It is also very advisable to have a backup of all your files. This way, you will not lose all your essential documents in case of a ransomware attack.
Step 3 – Work With A Professional Ransomware Recovery Firm If Malware Removal And Shadow Copy Recovery Fails
Due to the fact that Phobos uses military-grade encryption and the vast majority of attacks are paired with removal of all shadow copies, which makes alternative forms of recovery outside of direct decryption is next to impossible. Never negotiate directly with the criminals. Let an expert cybersecurity such as BeforeCrypt manage the situation and help you in recovering your precious data. A quick synopsis of Phobos Ransomware is essential and having a team of experts that are willing to speak with you to de-escalate the situation is primordial.
If you are interested in even more technology-related articles and information from us here at Bit Rebels, then we have a lot to choose from.


COMMENTS