Core coverage of emerging technologies, hardware, software, AI, security, and innovations shaping the future of the digital world.
5 Reasons Your Website Is Having Problems With Organic Traffic
Organic traffic, the type of traffic your website gets from appearing in search engine results, is one of the most valuable types of traffic a website can get, and it depends on the whims of search engines. Sure, some might say that paid traffic is more important for conversion rates, but if you're ...

5 Genius And Unconventional Ways To Use Technology
Technology is an ever-expanding universe of its own – yet, it takes some genius minds to use it in unconventional ways.
It’s true that the greatest minds of all time have worked hard to find uncommon solutions to common problems. The best minds can look at available technology and engineer ways t ...

7 Simple Ways To Always Keep Your Smartphone Safe
When it comes to our smartphones, many of us never think about our security when using them. It seems so unlikely that anything would happen when you’re using your smartphone, so why should you worry? Well, it turns out that there are plenty of reasons to worry when it comes to your smartphone and d ...

3 Awesome Technologies All Seniors Should Embrace
Seniors are known for being reluctant when embracing new technologies. Confusing, complex and different, there's something about technology that seniors shy away from. The issue is that a lot of these technologies can help better a senior's life.
What technologies should a senior embrace?
A lo ...
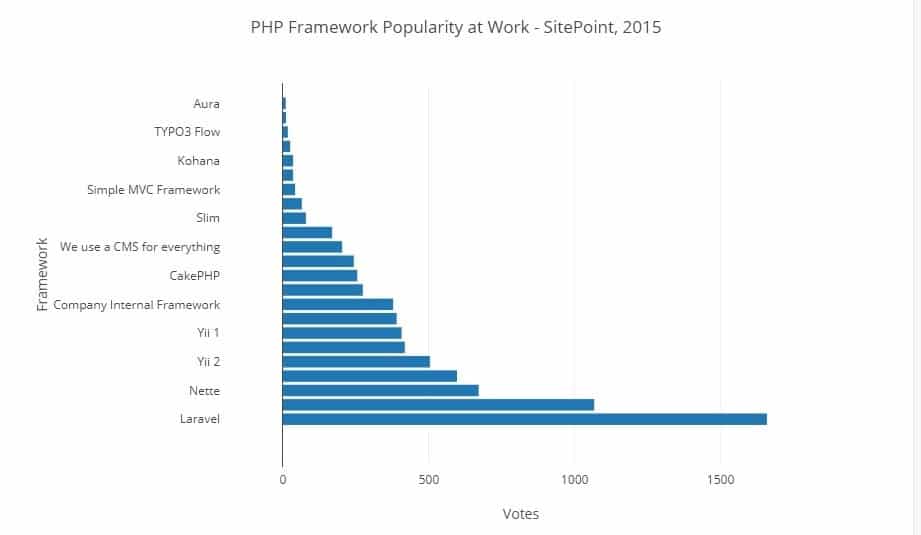
PHP Development With Laravel – Comparing The Pros And Cons
PHP was rather troublesome in the past. Poor syntax prompted those who develop quality web apps and websites to select other programming languages. Frameworks written in Ruby on Rails, Python and Django gained popularity because of their higher maturity. Now PHP is regaining momentum, and many web d ...

How To Unlock Your Samsung Galaxy Note 8 Smartphone
Unlocking a mobile phone permits buyers to move from your original service provider to the service provider of your choice. This will open your phone so that the phone can be utilized with a SIM card from an alternate carrier.
All through this report, the term unlocking will be utilized just to r ...

How Technology Can Help You To Motivate Yourself
Don’t worry, it isn’t just you – we all struggle to motivate ourselves. Sometimes we even need to motivate ourselves to do the things we really want to do. However, there are a lot of systems you can put in place to help you with your motivation, and there are a lot of nifty pieces of tech that can ...

5 Security Issues With Smart Homes You Should Know About
Smart homes or, a more technical labeling, connected home technologies with smart features have brought a new level of convenience to homes across the nation. However, with every added feature there are new security vulnerabilities that need to be considered. Houses may be getting smarter, but they’ ...

The Creative Use Of iPads In The Restaurant Industry
Despite the number of new smart devices entering the market, the Apple iPad remains a useful device, not only in the eyes of personal users but businesses as well. It is not uncommon for corporations to use the iPad as part of their business ecosystem. In fact, solutions built with iPads at their co ...

How To Keep Your House Cool In The Summer Months
It is a common practice among Americans to crank up the AC when the thermometer is rising close to the triple digits. What most Americans don’t know is that you can cool your home without the AC. Want to know how? Well, here are three secrets to help cool your home without an AC.
Secret #1 – Open Y ...

9 Things To Look For In A Good Subwoofer For The Home
When it comes to assembling a home theater system, one of the most components is the subwoofer and this isn't an item you want to choose based on price or convenience.
The subwoofer affects the quality of sound for the rest of the system, so it's important to choose a quality product. In choosing ...

Why Cybersecurity Training Should Never Be Overlooked
Cybersecurity is the process of identifying, responding, and stopping security breaches and other cyber incidents. Though cybercrimes can be both minor and major, there is always a negative effect on a business, individual, government, or community.
According to the Department of Homeland Securit ...
How To Fix Runtime Broker High CPU Usage In Windows 10
Can RuntimeBroker.exe be a virus? - No, it is not. The legal RuntimeBroker.exe document is a secure Microsoft Windows system procedure, known as "Runtime Broker." Writers of malware applications, by way of instance, viruses, worms, and Trojans intentionally give their methods the same file name to e ...

Cyber Security Device With Artificial Intelligence Component Hits Milestone
Press Release - Oasis Technology’s TITAN Cyber Security Defense Unit has now completed regional trials with Energy, Finance, and Medical industries and is now being rolled out nationally.
(CAMARILLO, CALIF) – Oasis Technology, a leading information technology, and cyber security company announces ...
![The Unstoppable And Incredible Rise Of Electric Cars [Infographic] The Unstoppable And Incredible Rise Of Electric Cars [Infographic]](https://bitrebels.com/wp-content/uploads/2017/08/unstoppable-rise-electric-cars-infographic-optimized.jpg)
The Unstoppable And Incredible Rise Of Electric Cars [Infographic]
Electric cars are projected to surpass traditional cars by 2040 according to figures in the infographic below from TopAutoTools. Demand for electric vehicles is expected to rise as their prices fall over time. More efficient manufacturing processes and the use of cheaper materials will cut costs mor ...